The use of SBOMs in medical device cybersecurity is integral to managing risks, vulnerabilities, and incidents effectively. By providing detailed visibility into software components, SBOMs enhance the ability of manufacturers and healthcare providers to maintain secure and resilient medical devices throughout their lifecycle. Adhering to regulatory guidance and industry standards ensures that the implementation of SBOMs meets the necessary safety and performance requirements.
The picture was borrowed from an article by Dmitry Ch
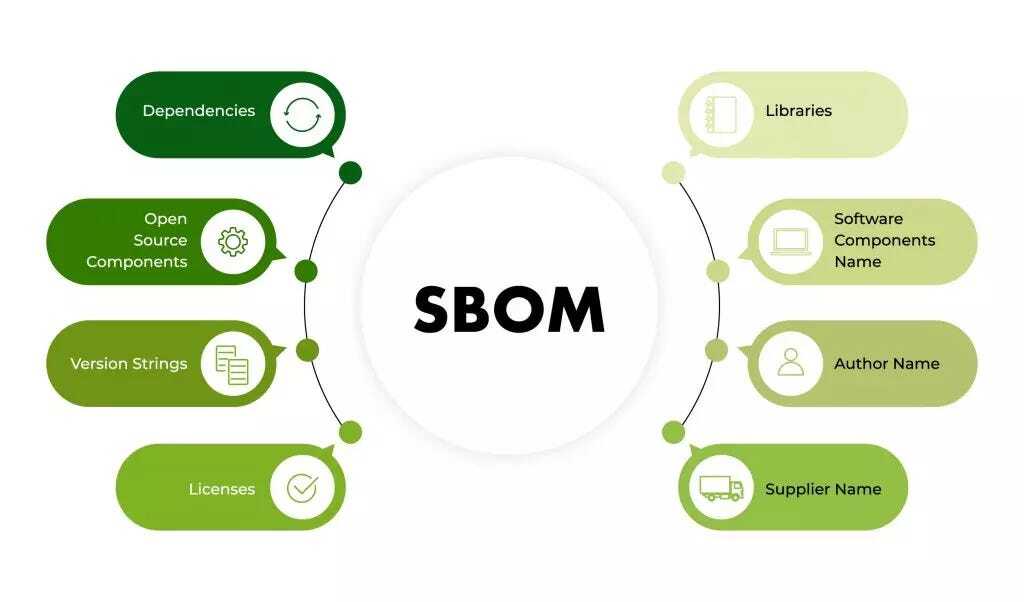
Purpose of SBOM:
- Identification of Components: An SBOM is essential for identifying all software components within a medical device, including third-party, open-source, and proprietary software. This aids in understanding dependencies and potential vulnerabilities.
- Risk Management: An SBOM supports risk management activities by providing detailed information about the software components, which can be cross-referenced with known vulnerabilities from external sources.
- Lifecycle Management: SBOMs are useful throughout the device lifecycle, from design to end-of-life, by helping manufacturers and healthcare providers manage updates, assess risks, and ensure continuous support for the software components.
SBOM Use Cases:
Risk Management:
Vulnerability Management:
Incident Management:
- Risk Evaluation: SBOMs assist in evaluating risks by identifying vulnerabilities in software components and assessing their exploitability and impact. This information helps in estimating the risk levels associated with specific vulnerabilities.
- Dependency Management: Understanding software dependencies (e.g., libraries, operating systems) is crucial. The SBOM helps in identifying dependencies that may introduce vulnerabilities into the device.
Vulnerability Management:
- Proactive Identification: SBOMs enable the proactive identification of vulnerabilities by regularly checking software components against vulnerability databases.
- Interim Mitigations: SBOM information allows healthcare providers to implement interim mitigations while manufacturers assess and develop updates to address vulnerabilities.
Incident Management:
- Efficient Response: An SBOM repository helps reduce the time required to identify and evaluate at-risk devices during a cybersecurity incident. This repository aids first-level support and cybersecurity teams in systematically collecting and correlating information to manage incidents more effectively.
Integration and Management:
SIEM Integration: Some Security Information and Event Management (SIEM) systems can directly ingest SBOMs if they are compatible with the SBOM formats, aiding in the correlation of security events.
Vendor Risk Management (VRM): SBOMs can be linked to VRM systems, enhancing the ability to manage vendor risks and correlate SBOM data with individual assets in the healthcare provider’s infrastructure.
Vendor Risk Management (VRM): SBOMs can be linked to VRM systems, enhancing the ability to manage vendor risks and correlate SBOM data with individual assets in the healthcare provider’s infrastructure.
Regulatory Guidance and Standards:
Regulatory Requirements: Various international standards and regulatory guidelines emphasize the importance of SBOMs for medical device cybersecurity, including documents from the FDA, European Commission, and other national health authorities.
Standards and Practices: Key standards such as ISO 13485, ISO 14971, and IEC 62304 provide frameworks for incorporating SBOMs into the risk management and quality management processes for medical devices.
Standards and Practices: Key standards such as ISO 13485, ISO 14971, and IEC 62304 provide frameworks for incorporating SBOMs into the risk management and quality management processes for medical devices.
